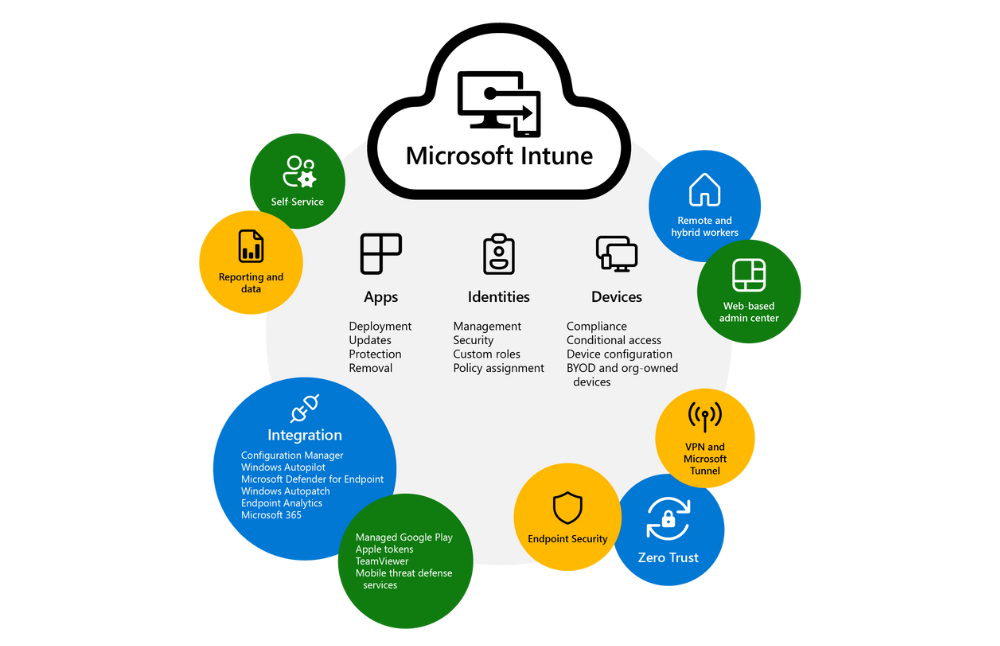
Microsoft Intune securely manages identities, manages apps, and manages devices As organizations move to support hybrid and remote workforces, they’re challenged with managing the different devices that access organization resources. Employees and students need to collaborate, work from anywhere, and securely access and connect to these resources. Admins need to protect organization data, manage end user access, and support users from wherever they work.
Microsoft Intune is a cloud-based endpoint management solution. It manages user access and simplifies app and device management across your many devices, including mobile devices, desktop computers, and virtual endpoints.
Key features and benefits
Some key features and benefits of Intune include:
1. You can manage users and devices, including devices owned by your organization and personally owned devices. Microsoft Intune supports Android, Android Open Source Project (AOSP), iOS/iPadOS, macOS, and Windows client devices. With Intune, you can use these devices to securely access organization resources with policies you create.
2. Intune simplifies app management with a built-in app experience, including app deployment, updates, and removal. You can connect to and distribute apps from your private app stores, enable Microsoft 365 apps, deploy Win32 apps, create app protection policies, and manage access to apps and their data.
3. Intune automates policy deployment for apps, security, device configuration, compliance, conditional access, and more. When the policies are ready, you can deploy these policies to your user groups and device groups. To receive these policies, the devices only need internet access.
4. Employees and students can use the self-service features in the Company Portal app to reset a PIN/password, install apps, join groups, and more. You can customize the Company Portal app to help reduce support calls.
5. Intune integrates with mobile threat defense services, including Microsoft Defender for Endpoint and third party partner services. With these services, the focus is on endpoint security and you can create policies that respond to threats, do real-time risk analysis, and automate remediation.
Integrates with other Microsoft services and apps
Microsoft Intune integrates with other Microsoft products and services that focus on endpoint management, including:
1. Configuration Manager for on-premises endpoint management and Windows Server, including deploying software updates and managing data centers You can use Intune and Configuration Manager together in a co-management scenario, use tenant attach, or use both. With these options, you get the benefits of the web-based admin center and can use other cloud-based features available in Intune.
2. Windows Autopilot for modern OS deployment and provisioning With Windows Autopilot, you can provision new devices and send these devices directly to users from an OEM or device provider. For existing devices, you can reimage these devices to use Windows Autopilot and deploy the latest Windows version.
3. Endpoint analytics for visibility and reporting on end user experiences, including device performance and reliability You can use Endpoint analytics to help identify policies or hardware issues that slow down devices. It also provides guidance that can help you proactively improve end user experiences and reduce help desk tickets.
4. Microsoft 365 for end user productivity Office apps, including Outlook, Teams, Sharepoint, OneDrive, and more Using Intune, you can deploy Microsoft 365 apps to users and devices in your organization. You can also deploy these apps when users sign in for the first time.
5. Microsoft Defender for Endpoint to help enterprises prevent, detect, investigate, and respond to threats In Intune, you can create a service-to-service connection between Intune and Microsoft Defender for Endpoint. When they’re connected, you can create policies that scan files, detect threats, and report threat levels to Microsoft Defender for Endpoint. You can also create compliance policies that set an allowable level of risk. When combined with conditional access, you can block access to organization resources for devices that are noncompliant.
Integrates with third party partner devices and apps
The Endpoint Manager admin center makes it easy to connect to different partner services, including:
1. Managed Google Play: When you connect to your Managed Google Play account, admins can access your organization’s private store for Android apps, and deploy these apps to your devices.
2. Apple tokens and certificates: When they’re added, your iOS/iPadOS and macOS devices can enroll in Intune and receive policies from Intune. Admins can access your volume purchased iOS/iPad and macOS app licenses, and deploy these apps to your devices.
3. TeamViewer: When you connect to your TeamViewer account, you can use TeamViewer to remotely assist devices.
With these services, Intune:
- Gives admins simplified access to third party partner app services.
- Can manage hundreds of third party partner apps.
- Supports public retail store apps, line of business (LOB) apps, private apps not available in the public store, custom apps, and more.
Enroll in device management, application management, or both
Organization-owned devices are enrolled in Intune for mobile device management (MDM). MDM is device centric, so device features are configured based on who needs them. For example, you can configure a device to allow access to Wi-Fi, but only if the signed-in user is an organization account.
In Intune, you create policies that configure features & settings and provide security & protection. The devices are fully managed by your organization, including the user identities that sign in, the apps that are installed, and the data that’s accessed.
When devices enroll, you can deploy your policies during the enrollment process. When enrollment completes, the device is ready to use.
For personal devices in bring-your-own-device (BYOD) scenarios, you can use Intune for mobile application management (MAM). MAM is user centric, so the app data is protected regardless of the device used to access this data. There’s a focus on apps, including securely accessing apps and protecting data within the apps.
Protect data on any device
With Intune, you can protect data on managed devices (enrolled in Intune) and protect data on unmanaged devices (not enrolled in Intune). Intune can isolate organization data from personal data. The idea is to protect your company information by controlling the way users access and share information.
For organization-owned devices, you want full control over the devices, especially security. When devices enroll, they receive your security rules and settings.
On devices enrolled in Intune, you can:
- Create and deploy policies that configure security settings, set password requirements, deploy certificates, and more.
- Use mobile threat defense services to scan devices, detect threats, and remediate threats.
- View data and reports that measure compliance with your security settings and rules.
- Use conditional access to only allow managed and compliant devices access to organization resources, apps, and data.
- Remove organization data if a device is lost or stolen.
Simplify access
Intune helps organizations support employees who can work from anywhere. There are features you can configure that allow users to connect to an organization, wherever they might be.
This section includes some common features that you can configure in Intune.
Use Windows Hello for Business instead of passwords
Windows Hello for Business helps protect against phishing attacks and other security threats. It also helps users sign in to their devices and apps more quickly and easily.
Windows Hello for Business replaces passwords using a PIN or biometrics, such as fingerprint, facial recognition. This biometric information is stored locally on the devices and is never sent to external devices or servers.